Running the Traefik, my favorite Edge Router with Podman

Today I'm going to show you how to use Traefik locally with Podman, my favorite Edge Router, to publish services with route matching, authentication, and other middlewares in an outstanding way.
Requirements
We require Podman to run containers locally; if you want an introduction, I wrote the following articles:


Podman SystemD Socket
Start the Podman systemd socket, as Traefik requires it to handle containers:
systemctl --user start podman.socketIf you prefer, you can set it to start immediately on boot:
systemctl --user enable podman.socketWhat is Traefik?
Traefik is a modern HTTP reverse proxy and load balancer developed in Go that is suited for microservice architecture. It is commonly used in containerized environments, such as Docker and Kubernetes.
There are no official Podman docs on how to make things work with Podman, although a few months ago I saw some examples using Podman Socket, similar to how Traefik works with Docker.
Traefik dynamically detects services as they are introduced to the infrastructure and routes traffic to them, making applications easier to manage and grow.
Major features:
- Automatic Service Discovery: Traefik can detect new services as they are introduced to your infrastructure, removing the need for human configuration.
- Dynamic Configuration: It can reorganize itself as services scale up or down, making it ideal for dynamic contexts like as container orchestration platforms.
- Load Balancing: Traefik includes built-in load balancing capabilities for distributing incoming traffic over many instances of a service.
- Automatic TLS: It may supply TLS certificates from Let's Encrypt, enabling HTTPS by default without requiring manual configuration.
- Dashboard: Traefik includes a web dashboard and a RESTful API, which enable operators to monitor and manage traffic routing and configuration.
- Middleware Support: It supports a number of middleware plugins for features like authentication, rate limiting, and request rewriting.
- Multiple Backends: Traefik can route traffic to multiple backend services based on various criteria like path, headers, or domain names.
Goals
The purpose is creating an example of using Podman Kube, a Kubernetes Deployment style to run pods. Traefik has a defined deployment schema. This article will introduce a way for annotating containers with labels.
Traefik communicates directly with Docker or Podman socket to listen for container creations and define routes and middlewares for them.
Please show the code that is working!

Deployments
- traefik.yaml
This file demonstrates a Traefik pod deployment that listens on ports 8000 and 8001.
apiVersion: v1
kind: Pod
metadata:
name: traefik
labels:
app: traefik
spec:
containers:
- name: traefik
image: docker.io/library/traefik:v3.0
args:
- '--accesslog=true'
- '--api.dashboard=true'
- '--api.insecure=true'
- '--entrypoints.http.address=:8000'
- '--log.level=info'
- '--providers.docker=true'
volumeMounts:
- mountPath: /var/run/docker.sock:z
name: docker_sock
ports:
- containerPort: 8000
hostPort: 8000
protocol: TCP
- containerPort: 8080
hostPort: 8001
protocol: TCP
restartPolicy: Never
dnsPolicy: Default
volumes:
- name: docker_sock
hostPath:
path: "/run/user/1000/podman/podman.sock"
type: File
Please check the location of your podman.sock, the default user is 1000, and the sock is typically found in /run/user/1000/podman/podman.sock.
- whoami.yaml
This file shows a replica of a simple HTTP container that returns container-specific information such as IP and host name for debugging.
Traefik uses container labels or annotations to define rules.
- traefik.http.routers.whoami.rule: specifies match rules for reaching the container, which can be host, header, path, or a combination of these.
- traefik.http.services.whoami.loadbalancer.server.port: specifies the port on which the container is listening.
apiVersion: v1
kind: Pod
metadata:
name: whoami
labels:
traefik.http.routers.whoami.rule: Host(`whoami.localhost`)
traefik.http.services.whoami.loadbalancer.server.port: 3000
spec:
containers:
- name: whoami
image: docker.io/traefik/whoami:latest
ports:
- containerPort: 3000
protocol: TCP
env:
- name: WHOAMI_PORT_NUMBER
value: 3000
restartPolicy: Never
dnsPolicy: Default
🫠Unfortunately, replicas are not supported. If we had replicas, Traefik would handle them using round-robin to reach each container, as Traefik works with Docker Swarm and Kubernetes.
- whoami-secure.yaml
This file describes the same service but includes the Basic Auth middleware to demonstrate how to utilize middlewares.
- traefik.http.routers.{route-name}.middlewares: specifies the middlewares utilized in the current container.
- traefik.http.middlewares.{middleware-name}.basicauth.users: specifies the user and passwords.
You can generate htpassword with the following command:
docker run --rm -ti xmartlabs/htpasswd <username> <password> > htpasswd
apiVersion: v1
kind: Pod
metadata:
name: whoami-secure
labels:
traefik.http.routers.whoami-secure.rule: Host(`whoami-secure.localhost`)
traefik.http.services.whoami-secure.loadbalancer.server.port: 3000
traefik.http.routers.whoami-secure.middlewares: auth
traefik.http.middlewares.auth.basicauth.users: foo:$2y$05$.y24r9IFaJiODuv41ool7uLyYdc4H4pDZ5dSKkL.Z/tUg3K3NancS
spec:
containers:
- name: whoami-secure
image: docker.io/traefik/whoami:latest
ports:
- containerPort: 3000
protocol: TCP
env:
- name: WHOAMI_PORT_NUMBER
value: 3000
restartPolicy: Never
dnsPolicy: Default
It is critical to note that only Traefik exposes a port to hosting; Traefik centralizes all traffic, proxying each request dealing with IP and listening port from each container.
Running
podman play kube pods/traefik/traefik.yaml
podman play kube pods/traefik/whoami.yaml
podman play kube pods/traefik/whoami-secure.yaml
Testing
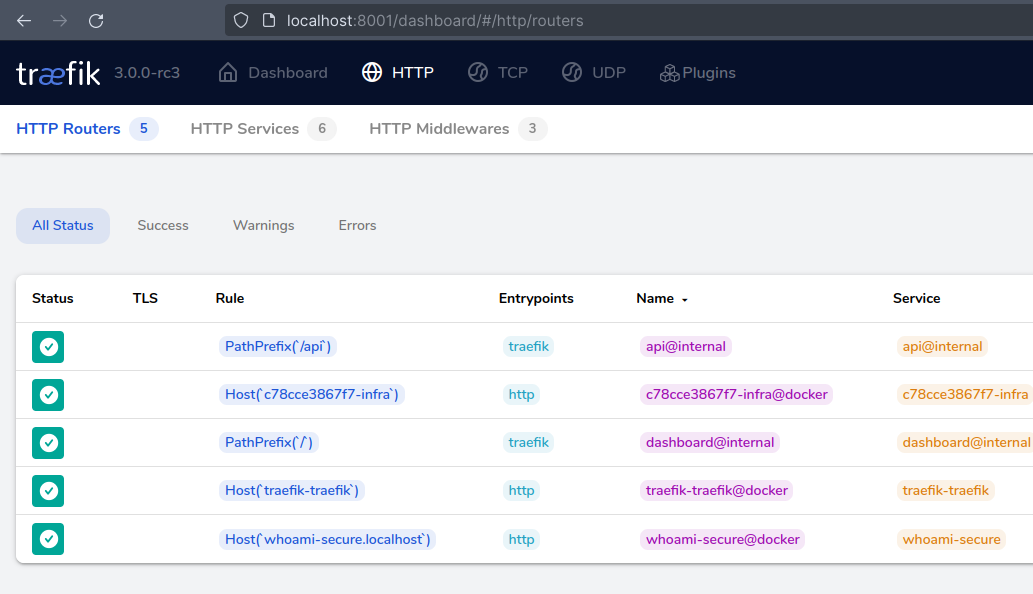
You can view Traefik Dashboard at port 8001, which displays importing information about Routes and Containers.
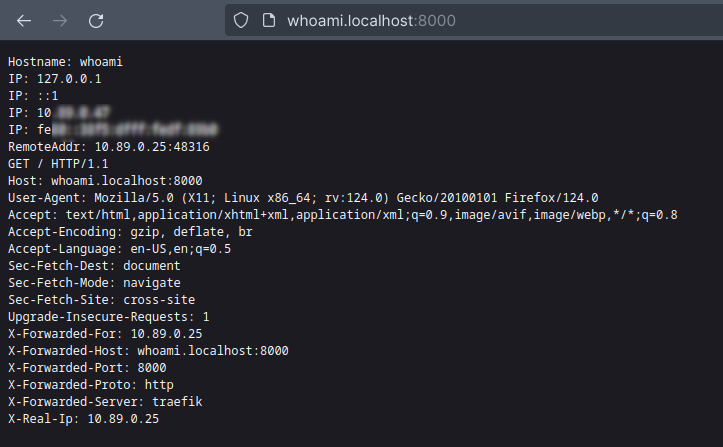
Let we test the Whoami route at endpoint http://whoami.localhost:8000/:
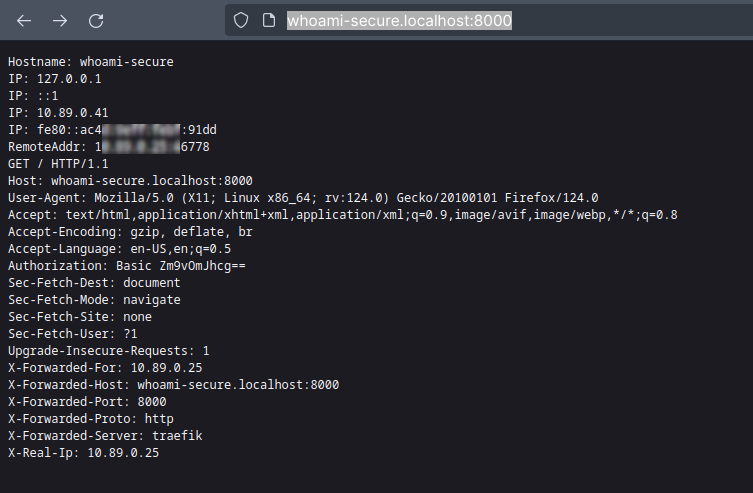
We can now check the Whoami route using basic authentication with the username "foo" and password "bar" at http://whoami-secure.localhost:8000/
Troubleshooting
If hosts is not resolving you may need to add to /etc/hosts.
127.0.0.1 localhost whoami.localhost whoami-secure.localhost
Code
💡 Feel free to clone this repository, which contains related files:
Tearing down
podman play kube --down pods/traefik/traefik.yaml
podman play kube --down pods/traefik/whoami.yaml
podman play kube --down pods/traefik/whoami-secure.yaml
That's it
In this post, we will demonstrate how Traefik works, how to build settings to reach containers, and how to use middleware to use the full capability of container orchestration. I recommend that you look into Traefik middlewares; they can be more beneficial than an API Gateway at times.
Please keep your kernel 🧠 updated God bless 🕊️ you. I'll share a quote:
Whatever you do, work at it with all your heart, as working for the Lord, not for human masters. Colossians 3:23

Time for feedback!